Common causes of data breaches in software solutions
Data breaches pose a significant threat to the integrity and security of software solutions for businesses of all sizes, across all industries. A breach is an incident where unauthorised individuals gain access to sensitive and confidential data, often leading to the compromise of information security. These can occur in various contexts, affecting organisations, businesses or individuals. The compromised data may include personal information, financial details, intellectual property, or any other data that is considered confidential.
Understanding the common causes of data breaches is crucial in fortifying your defences against potential threats. These are the most common causes in software solutions:
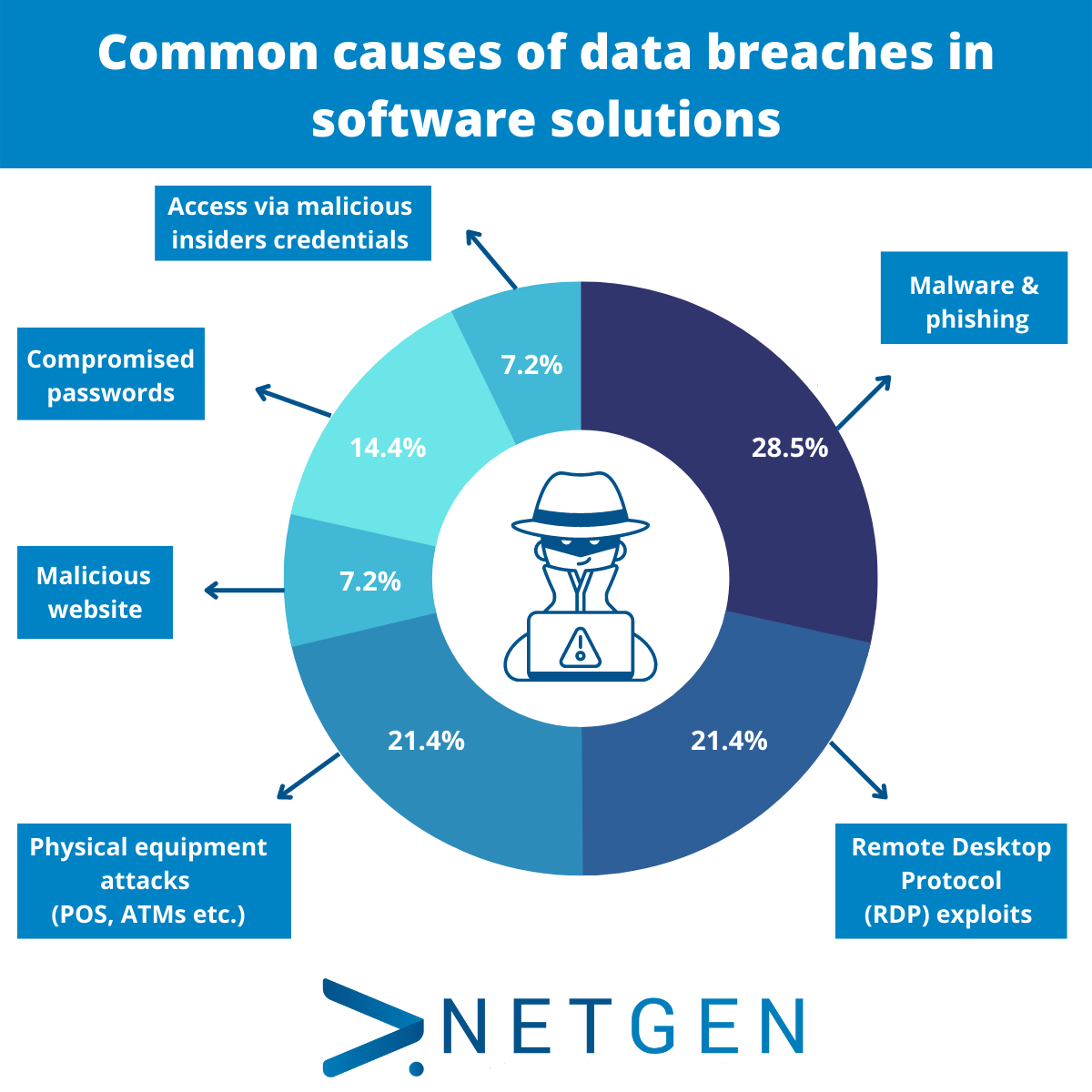
- Malware and phishing – Educating users about the risks associated with opening suspicious emails, and implementing robust anti-malware solutions are essential steps in mitigating these threats.
- Remote Desktop Protocol (RDP) exploits – These exploits provide attackers with a direct route into a system. These can be countered by using strong authentication methods, regularly updating RDP software, and monitoring for any suspicious activity.
- Physical equipment attacks – Physical attacks on equipment like Point of Sale (POS) systems and ATMs can lead to unauthorised access and data breaches. Implementing physical security measures, such as surveillance and tamper-evident technologies, can help protect against these types of attacks.
- Compromised passwords – Weak or compromised passwords are a major gateway for cybercriminals. Ensure that secure password policies are enforced and that multifactor authentication (MFA) is implemented where possible.
- Malicious websites – Malicious websites are a breeding ground for various cyber threats. Users may inadvertently download malware or fall victim to phishing attacks while browsing compromised sites. Ensure that firewalls and web blocking software is kept up to date.
- Access via malicious insider credentials – A malicious insider could be a disgruntled employee, a contractor, or any individual with legitimate access to sensitive information. Strict access controls and regular monitoring of user activities can help detect and prevent unauthorised access.
Netgen guards against data breaches
At Netgen, security is paramount. Whether we’ve developed a custom software solution, mobile app, or website, you can rest assured that we’ve taken every precaution against data breaches and other cyberthreats. Contact us today to find out more.

